These terms are subject to frequent discussions nowadays, both in private conversations and media coverage - but do we all understand them the same way? What do they mean precisely in terms of being online - for internet users and service providers? This article is an attempt to answer these and other similar questions, and present our team's point of view.

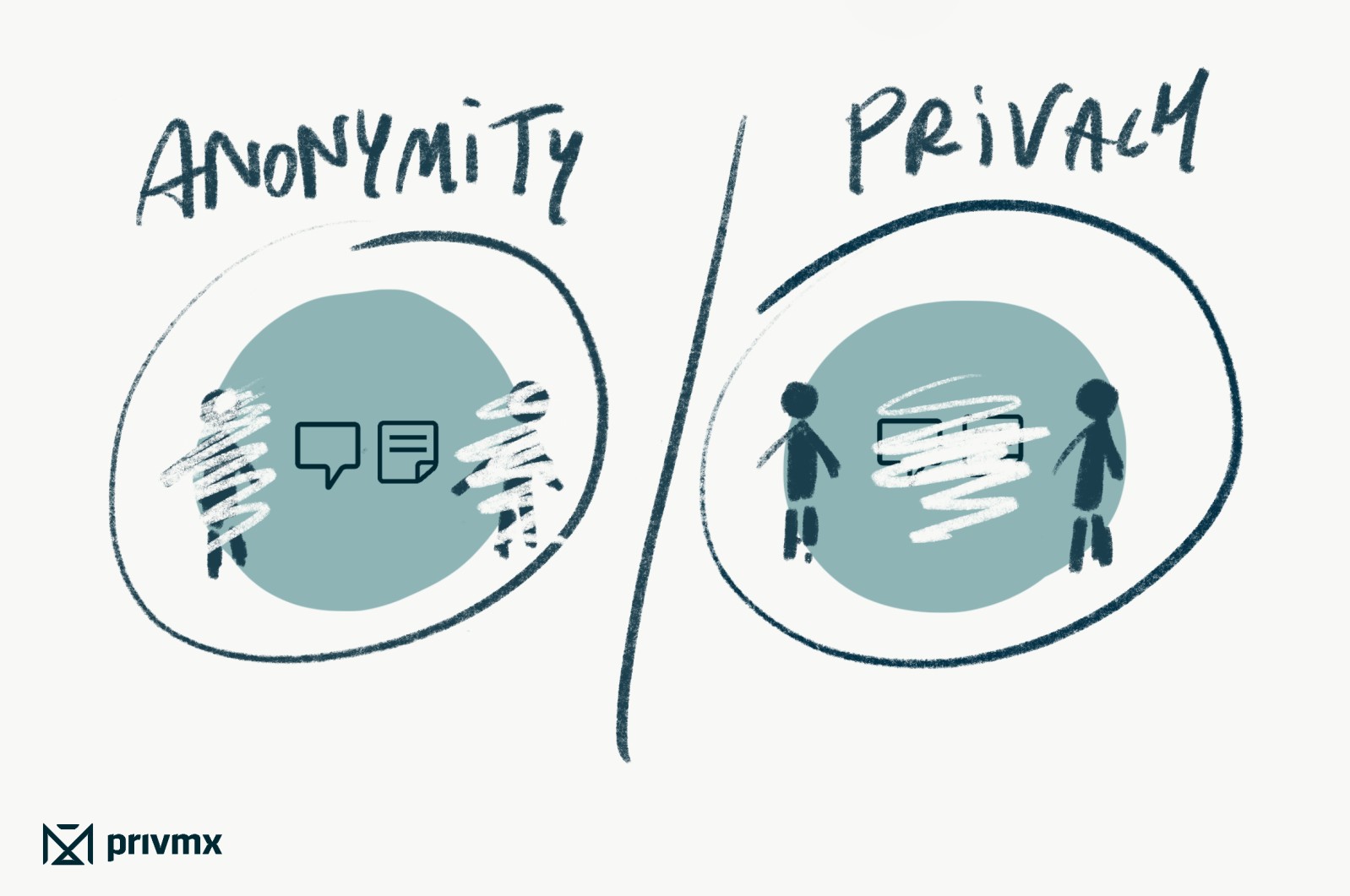
In PrivMX team, we often talk about how it is becoming more and more common to equate "privacy" with "anonymity". Companies offering private data storage and/or communication services collect negative comments from dissatisfied customers who think that if a given service has something to do with privacy, it means that people who use it become anonymous.
We think that it’s a kind of misunderstanding and one may be wondering what is the reason for this, but as suppliers, we must above all try to prevent such situations from taking place. Appropriate knowledge should be an integral part of our service, reaching our customers not only in the form of appropriate provisions in the privacy policy, that in fact is read by few people.
In this article, we aim to present a brief description of our (PrivMX) position on online privacy and anonymity. Hopefully, it will help many people gain a broader perspective of how things really are.
What are the characteristics of any live, Internet or telephone private conversation? It is usually a free exchange of certain content that we want to keep to ourselves, but pass it on to other people we trust and to no one else during the conversation. It almost never means a secret conversation, one in which the environment cannot see WHO is having the conversation - the more important thing is that the CONTENT of the conversation remains private, “for your eyes / ears only”.
This type of behaviour is natural for us (people) and that is why we believe that the privacy of correspondence (content) is a natural human right that cannot be violated, and even less, permanently abolished. Personal private spheres define us as separate people, thus creating a diverse, wonderful and versatile community.
Creating PrivMX, our team is trying to understand and implement the issue of privacy from the very beginning, as described above. However, we extend it and organize around teams of people creating joint ventures, working together for a long time on their own affairs.
We believe that our greatest treasure as humanity, one that we don’t care for enough in this digital 21st century, is what millions of teams around the world are working on. The most creative, complex and valuable ideas are created during teamwork — and those ideas, in combination with others, improve our world, offering team members a way to live and support their families.
Therefore, we should ensure the privacy of content created by teams the same way we naturally try to protect our personal affairs. It is up to the team to decide when, how, to whom and on what conditions they want to give physical insight into the content of their conversations and deliberations, as well as access to the results of their many months of work. In a distributed, digital work environment of the 21st century, you can try to take care of it by taking care of "workstation hygiene" and using software with appropriate features, with the key one being, in our opinion, end-to-end encryption for all content created, stored and sent inside the team.
In our understanding, anonymity means something different than privacy -first and foremost, it is a concern about the "invisibility" or “non-traceability" of a person or people - for the environment, for the system. From time to time, we all probably come across anonymous activities and content from unspecified people. In such situations, the privacy of the content usually does not matter or is even deliberately bypassed to make the content as public as possible. We don't want to go deeper into this topic here, and instead, below we try to tackle a key, central question about anonymity: is anonymity possible at all, in the digital 21st century?
The short answer is: in our opinion, one can only try to talk about anonymity as a consequence of adopting one of the two extreme paths. The first way is to completely deprive yourself of electronic devices and conduct meetings where civilisation has not reached - e.g. in the forest. The other way is the opposite extreme - equipping yourself with IT tools and professional skills usually presented by hackers, allowing to hide, to some extent, in the digital web.
The problem, however, is that both approaches are far from how and where we actually live - in the digital world of identifiers, AI-connected cameras, transaction logs, geolocation, and hundreds of other devices, databases and algorithms that record our actions. Of course, we keep fighting for our data (e.g. personal data) to be under any control, at least legal (see GDPR), but announcing any decisive, real successes in this field would rather be the result of wishful thinking than any rational deduction.
The Internet has a specific structure - in order for one computer (e.g. your laptop) to connect to another computer (e.g. a website server), it must do so through several intermediary devices, situated in different geographic locations. Each of these devices has access to the knowledge about the connection it is taking part in, and we should assume that there may always be someone in the world who is able to make an effort and find out which computers on the Internet you have connected to with your laptop. The information about our connections can be partially controlled by the use of dedicated intermediary services (which is worth mentioning here for the sake of completeness) - however, it does not change the overall situation too much. The use of intermediary services (such as VPN, TOR, etc.) should not be understood as "obtaining anonymity on the Internet", but only as entrusting your online identity to a third-party company or other group of people who have access to intermediary devices.
The general picture that we’re outlining here will not seem too optimistic for many people, but we should all remember these facts because it is the healthiest, truth-based approach to using the Internet. But how does this relate to what we do as PrivMX?
As we mentioned above, PrivMX is focused on providing companies and teams with a digital collaborative environment for the 21st century. In our case, the situation is simple - hard-working teams, by their nature, want to control who has access to their valuable resources and therefore the anonymity of team members is not a feature/function in our software. However, it is not excluded - connections with PrivMX team servers are also possible through the mentioned intermediary services, which to a greater or lesser extent anonymise the source of the connection.
Finally, it is worth mentioning that our software can also be used in a self-hosted version, and in this situation, the control of all the described issues - intermediary devices and anonymity - lies entirely within the organisation using PrivMX.
PrivMX focuses on the privacy of teams - it protects all their data on servers and intermediaries from unauthorised access - by using end-to-end encryption.
PrivMX does not deal with the anonymity of team members and connections - we believe that this is not possible under normal circumstances in the 21st century, but on the other hand, PrivMX does not in any way block attempts to use external anonymization services.
We hope this short article will give you a different perspective on anonymity and privacy. When using the Internet - at work or at home - it is worth trying to look a little deeper into this complicated technology. Ultimately, it is supposed to be a tool for our use, not the other way around.
 Matt Muszytowski
Matt Muszytowski
 Similar blog posts:
Similar blog posts:

Encryption in-transit, encryption at-rest, end-to-end encryption and zero-knowledge encryption: different types of encryption in a nutshell.
Meet PrivMX Pocket - a mobile companion app for our desktop application, available for IOS and Android. There's also an important update on the file chooser and Sections' export.